Application Networks

Corda, as previously described, is a private, permissioned, DLT Distributed Ledger Technology. A type of database technology that enables a network of computers to maintain a shared and synchronized database. platform. An application network is a discrete instance of a permissioned collective associated with one or more applications.
Unlike public DLT platforms such as Ethereum, where the ability to use the system is open to all, access to a Corda system is gated by the entity/entities (known as the Network Operators) operating the network. This network is associated with a CorDapp Corda Distributed Application. A Java (or any JVM targeting language) application built using the Corda build toolchain and CorDapp API to solve some problem that is best solved in a decentralized manner. , where the members of the network are allowed to utilize the system for some purpose. The specific rules specifying how an identity is allowed to join are left to the operator to determine. However, once permitted to join, each member understands that each other member has had their identity challenged to the same extent.
The severity and extent of that attestation are, as previously mentioned, left to the Network Operator, but should reflect the needs of the CorDapp being operated by the network and can range from allowing anyone to join unchallenged to performing a full KYC process on each request.
The following diagram shows the application network architecture:
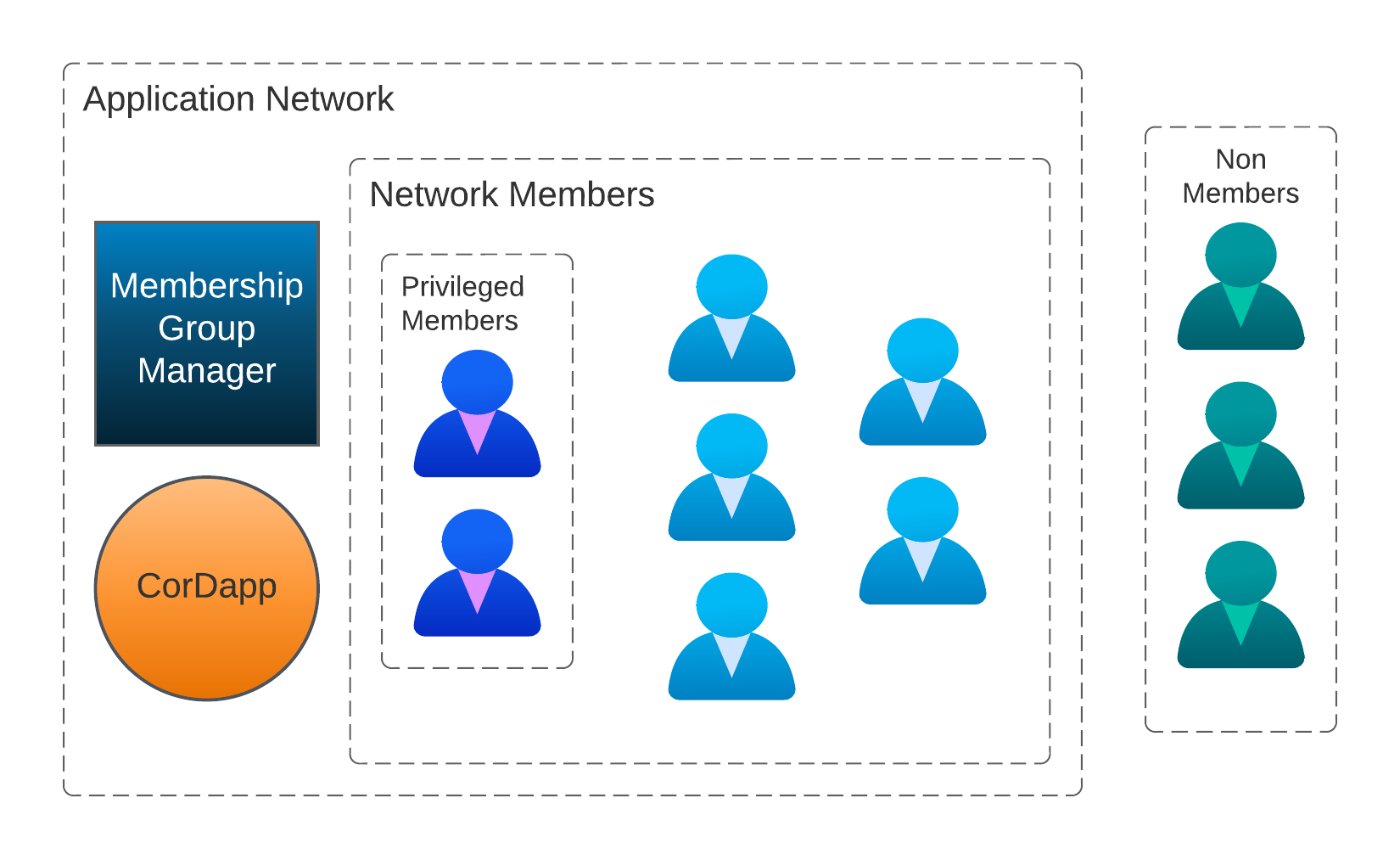
Identity Attestation

The Membership Group Manager ( MGM Membership Group Manager. May also be referred to as the Network Manager. It is a virtual node and Corda identity that acts as a central registrar for group membership. ) permits identities into an application network. Identities wishing to join present a request containing various metadata describing them but, most importantly, their unique name and their location as an IP address.
Whilst not strictly required, it is encouraged that alongside their name, identities submit a PKI Public key infrastructure. A comprehensive system of hardware, software, policies, and procedures that enables the secure creation, distribution, management, and revocation of digital certificates and public-key cryptography. certificate issued by a trusted authority, alongside the public key whose signature represents the identity’s affirmation of acceptance.
The process of attestation is simple: identities submit their request, additionally request an escalated role, and the Network Operator either approves or declines the request.
Identity Uniqueness

It is important within an application network that each identity is uniquely addressable and so each identity must present to the network a unique name. Corda does not allow duplicate names to join a single application network. However, the same name may exist in multiple different networks, especially if representing the same entity An organization or individual that participates in one or more application networks that can provide attestation that they are whom they claim to be. . This is enforced at the platform level.
Peer-to-Peer Communication

As shown below, Corda is different from other distributed ledger A database of facts that is replicated, shared, and synchronized across multiple participants on a network. systems in that all communication between nodes is peer-to-peer, and only shared on a need-to-know basis. It is also encrypted using TLS Transport Layer Security. A protocol that establishes an encrypted session between two computers on the Internet. . There are no global broadcasts to all nodes on a network, but all nodes in a network can send messages directly to each other. If the recipient is offline, the message waits in an outbound queue until they are online again, just like an e-mail.
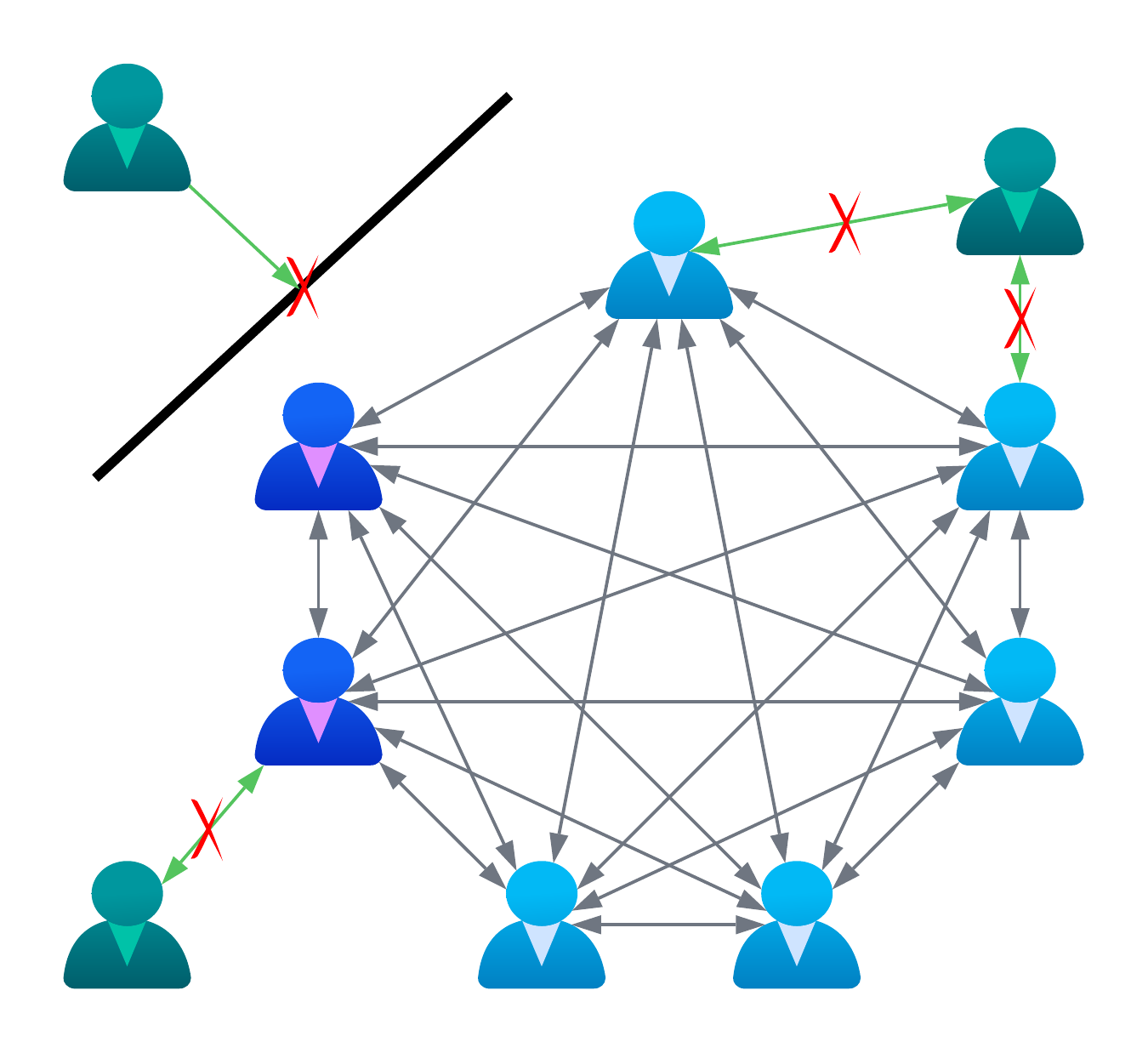
Identities not registered as members of the application network cannot communicate with those that are, even if they obtain a copy of the CorDapp code:
- The identities may not be externally visible outside of the application network.
- The reverse connection attestation undertaken by the Corda networking layer ensures that only attested identities can communicate.
Privacy

Communication

Through its attested identity model, Corda allows for direct peer-to-peer messaging between identities. A proposal to mutate the global state can be undertaken without the knowledge of those not a party to that mutation; there is no need to globally broadcast updates and thus avoid leaking sensitive information. At any single point in time, an identity can be involved in any number of distinct transactions:
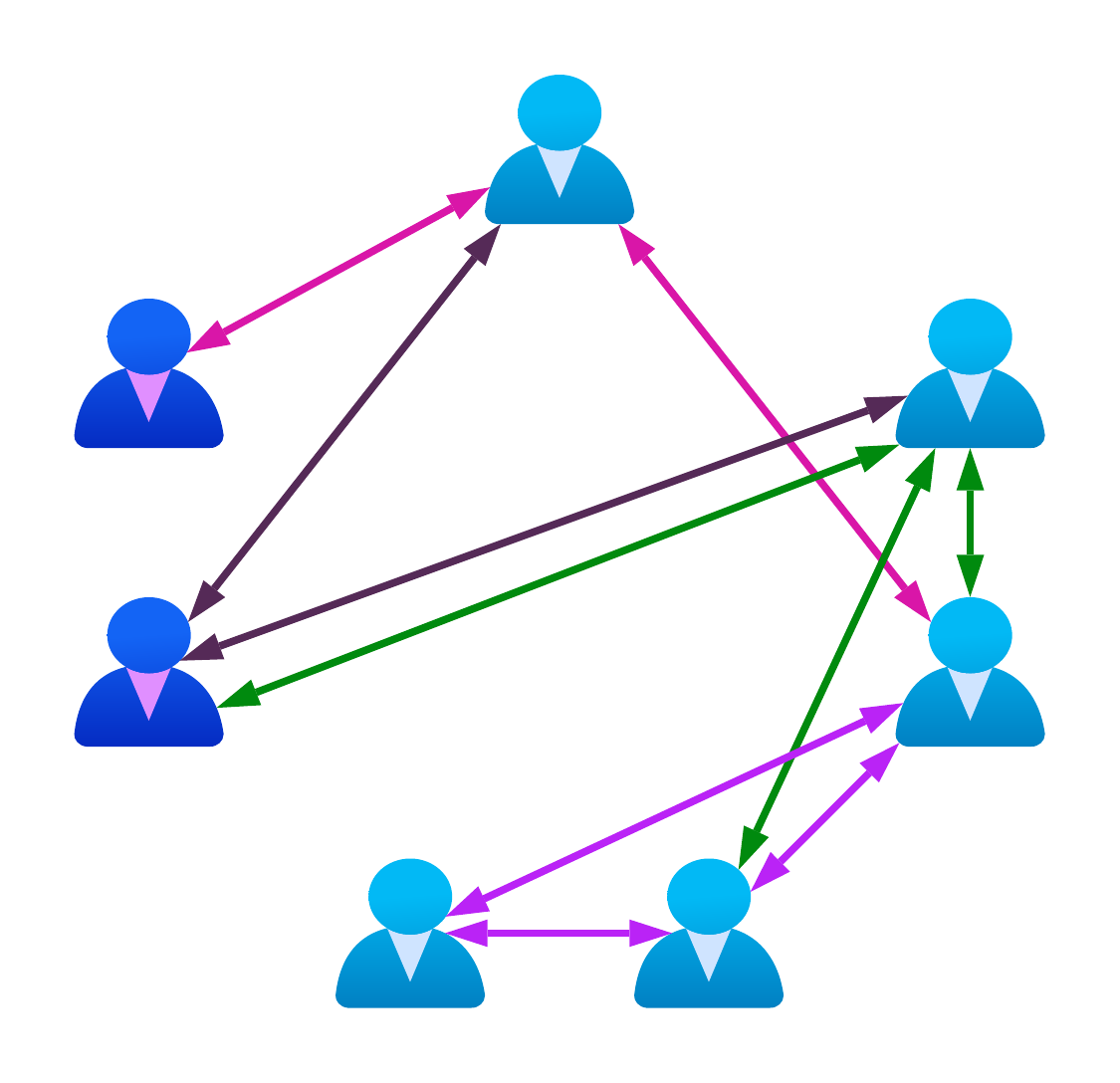
Global State

In Corda, as in all DLT Distributed Ledger Technology. A type of database technology that enables a network of computers to maintain a shared and synchronized database. systems, there exists a global state. However, in Corda, that global state is not globally visible. Each participant’s identity only has visibility over those portions of the global data that are relevant to it:
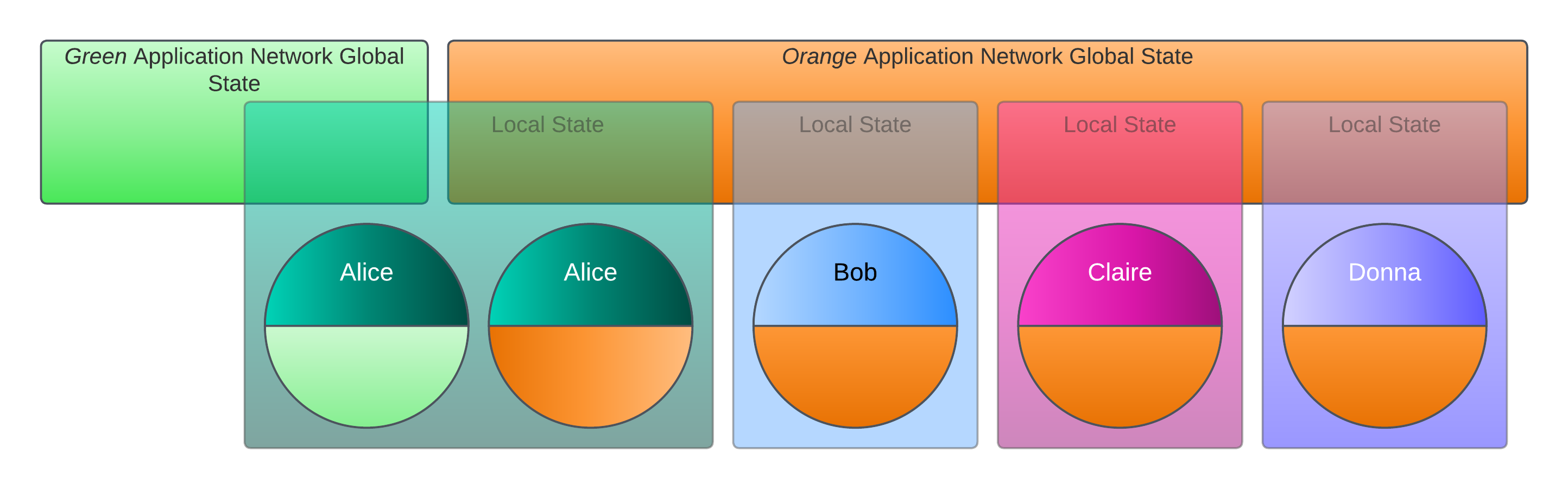
As shown in the following diagram, there is no single storage point or distribution of data globally. Each identity locally stores the slices of the global state it needs to, either because:
- it is a direct participant in a mutation of the global state.
- it was added as an interested party by a participant.
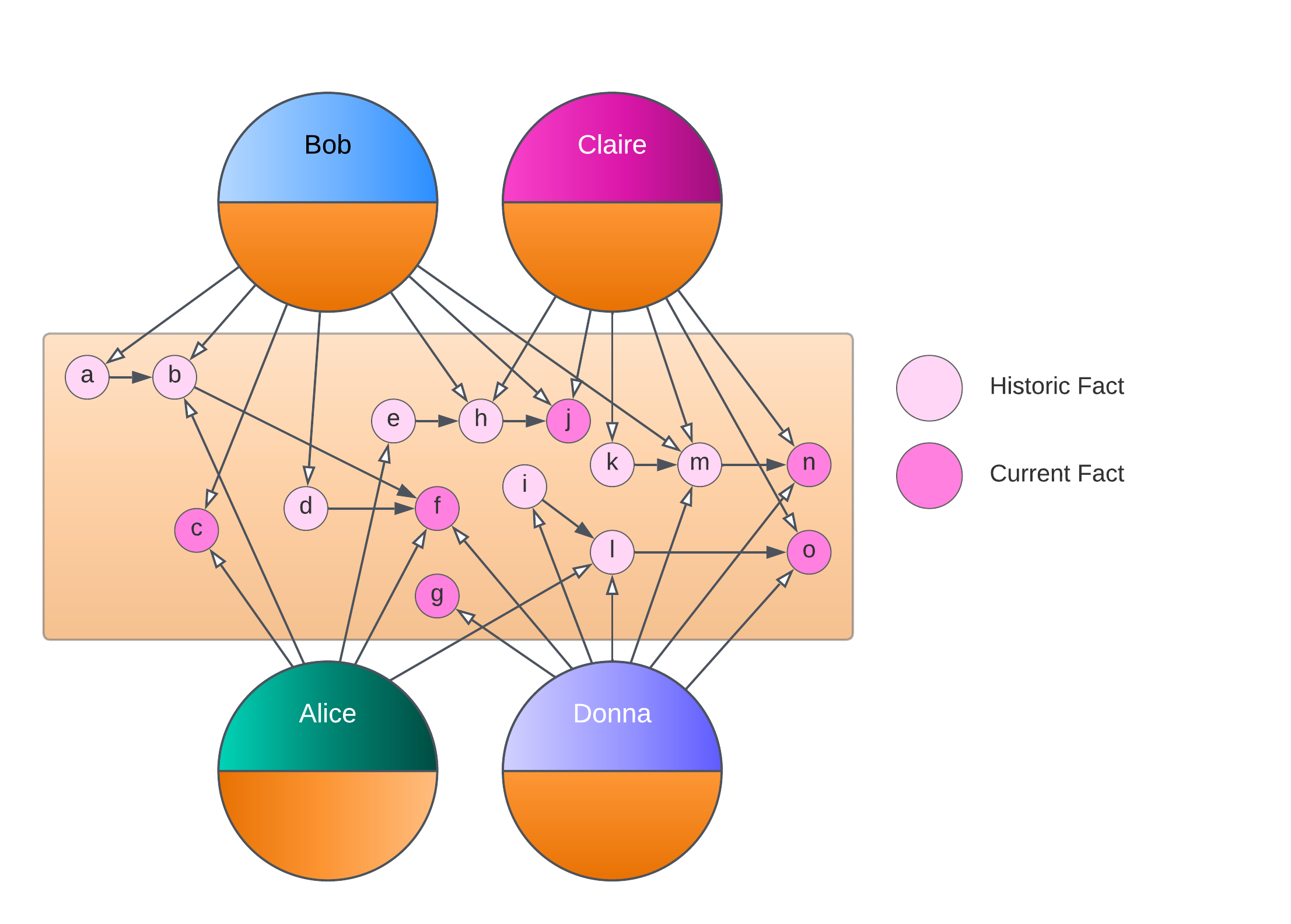
Therefore, multiple copies of data are distributed and replicated where needed:
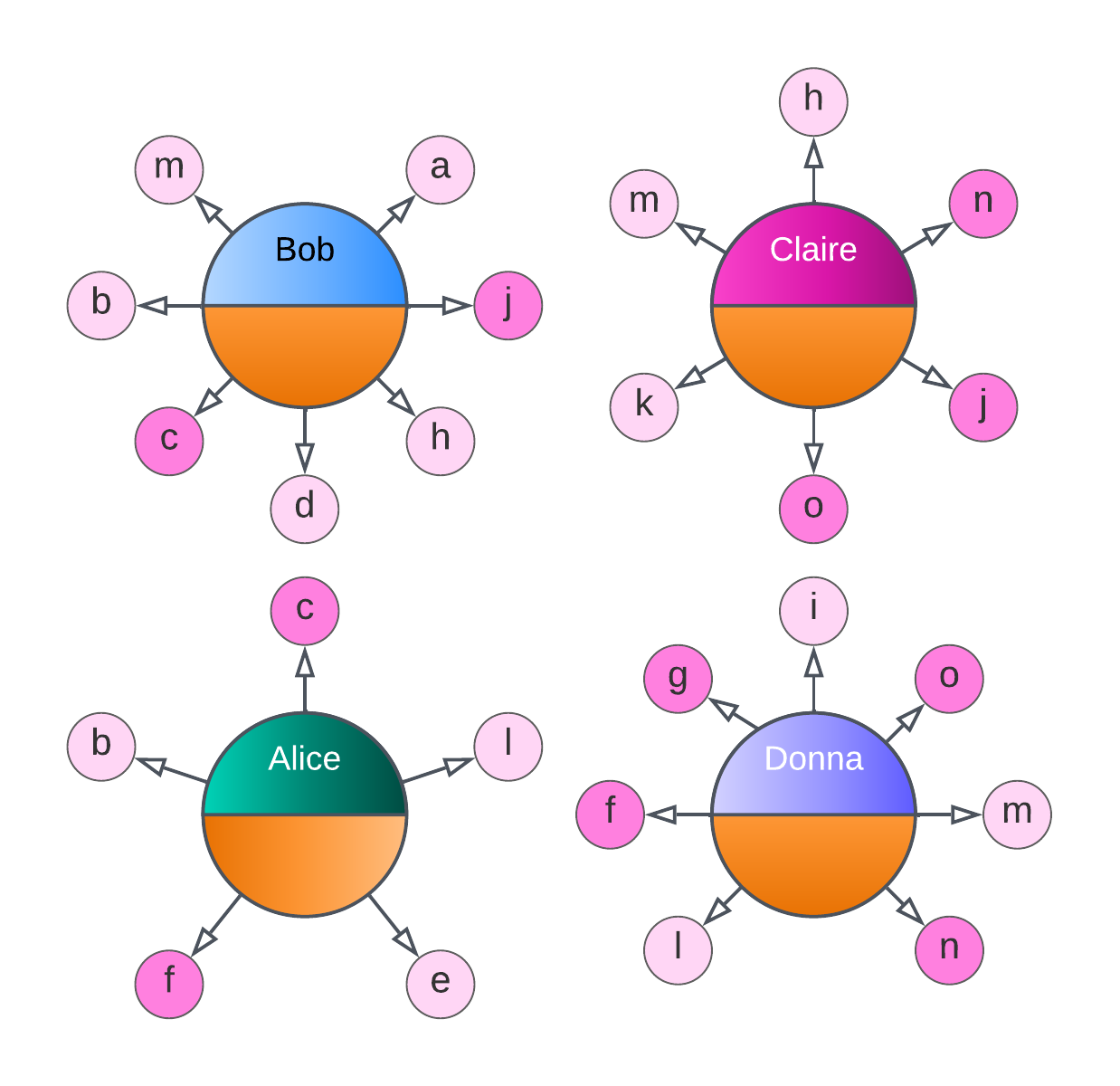
Ultimately, the fundamental promise of Corda and all DLTs is that, once committed to the global state and accepted as valid, there can be no disagreement that an event has occurred:
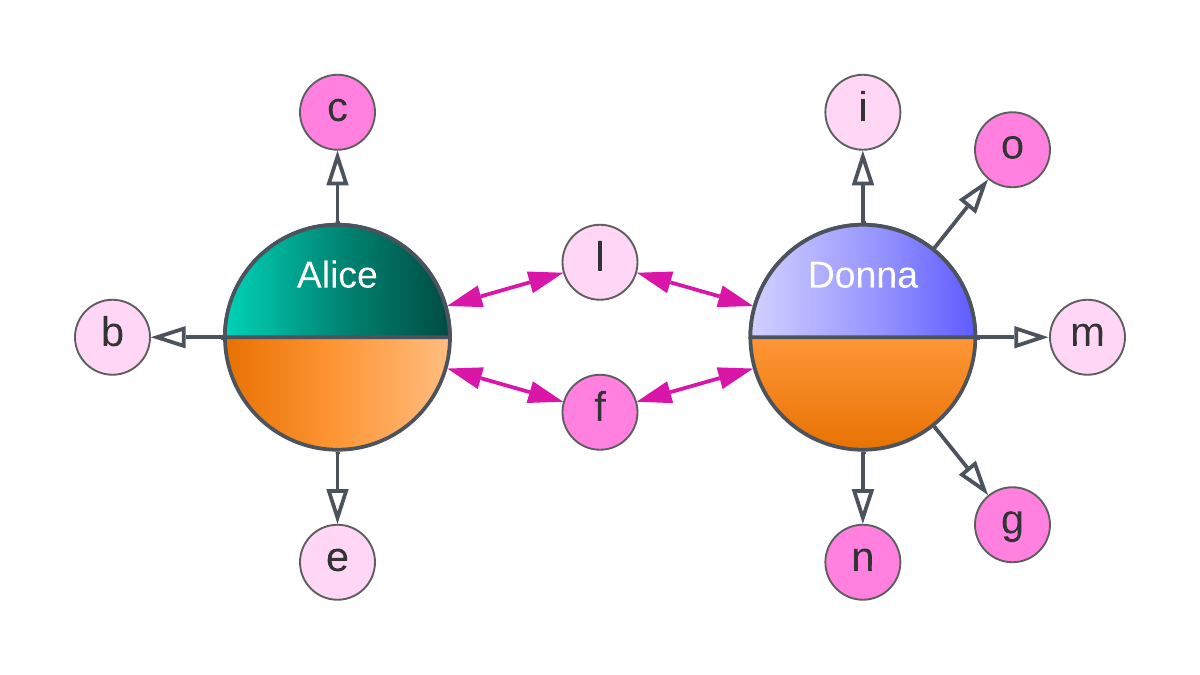
Reconciliation is not needed as there is a single accepted version of valid that has been attested by all parties and that those with visibility trust.
Was this page helpful?
Thanks for your feedback!
Chat with us
Chat with us on our #docs channel on slack. You can also join a lot of other slack channels there and have access to 1-on-1 communication with members of the R3 team and the online community.
Propose documentation improvements directly
Help us to improve the docs by contributing directly. It's simple - just fork this repository and raise a PR of your own - R3's Technical Writers will review it and apply the relevant suggestions.
We're sorry this page wasn't helpful. Let us know how we can make it better!
Chat with us
Chat with us on our #docs channel on slack. You can also join a lot of other slack channels there and have access to 1-on-1 communication with members of the R3 team and the online community.
Create an issue
Create a new GitHub issue in this repository - submit technical feedback, draw attention to a potential documentation bug, or share ideas for improvement and general feedback.
Propose documentation improvements directly
Help us to improve the docs by contributing directly. It's simple - just fork this repository and raise a PR of your own - R3's Technical Writers will review it and apply the relevant suggestions.